Abstract
The Jesuit scholar, Roberto Busa, is often called the founder of humanities
computing. In fact, starting as early as 1949, he collaborated with IBM to
perform experiments using suites of punched-card machines. These punched-card
data systems—with their plug-board setups, clacking machinery, and flurries of
perforated rectangular cards—were developed for business accounting and
tabulating, and adapted for government censuses, defense calculations, archival
management, and information processing of all kinds. The first decade of
humanities computing can more accurately be described as an era of humanities
data processing—in the historically specific and contextually rich sense of the
term. This essay describes an ongoing collabroative project that aims to reverse
engineer that center in the attempt to understand better this important site in
the history of technology and humanities computing.
In March 2015 I visited a gated courtyard building on a quiet street in Gallarate,
Italy, the via Galileo Ferraris, no. 2.
[1] It had once extended
into a larger building, now demolished. When I arrived that day the remaining
building was covered in scaffolding and dust, in the process of being converted into
a charity residence (
Figure 1). But based on the address and some
distinctive architectural features, I confirmed that it was the site of what’s
usually considered the first humanities computing center. This was where the Jesuit
scholar Father Roberto Busa created and supervised CAAL, the
Centro per L’Automazione dell’Analisi Letteraria — the Center for the
Automation of Literary Analysis (or Literary Data Processing Center, as it was
sometimes translated) — which operated there 1961-1967. What follows describes an
ongoing effort to conceptually
reverse engineer that center in an
attempt to better understand this important site in the history of humanities
computing.
Reverse engineering is a method for learning about something by taking it apart. It’s
often applied to lost, secret, or otherwise obscured technologies. You take apart a
device or a component in order to learn how it was put together. It’s a kind of
hands-on conjecture, a way provisionally to “write the missing
manual.” You work backwards from a given concrete object to
reconstruct its possible abstract design, tinkering in pursuit of better
understanding. As one introductory essay on the topic says: “While conventional engineering transforms engineering
concepts and models into real parts, in reverse engineering real parts are
transformed into engineering models and concepts”
[
Varady et al. 1997]. Those “models and concepts” are necessarily based on some
degree of speculation and are bound to remain uncertain. Nowadays, reverse
engineering involves software as well as hardware (both in targeted object and
method). Even when applied to a physical object, the process is likely to employ
both digital and physical, including materials different from those of the original
targeted object — for example, extruded polymers from 3D printers, clay, or
Styrofoam — as well as virtual models built in software, including immersive 3D
models. In fact, the use of CAD/CAM systems (Computer Aided Design/Manufacture) has
become the norm in reverse engineering of all kinds [
Varady et al. 1997].
Common in everyday prototyping, design, and manufacture, reverse engineering has also
been associated with industrial or state espionage, as a way of modeling classified
or proprietary devices or systems. The German Enigma machine of World War II, an
electro-mechanical encryption/decryption device, is a famous example. In fact,
classic cryptanalysis is itself a form of reverse engineering applied to systems of
symbols, but also, as in the case of the Enigma, the machines used to process those
symbols. Reverse engineering has affinities with a number of historical and
conjectural practices applied to objects and systems obscured by time and whose
contexts are lost, for example, textual criticism, which often requires a scholar to
fill in gaps left by textual lacunae, lost witnesses, or blotted, foxed,
overwritten, or otherwise obscured passages in manuscripts.
The basic concept of reverse engineering is familiar in digital humanities, too, as
part of the field’s emphasis on experiment, making, and prototyping.
[2] Jentery Sayers
and others at the University of Victoria’s Maker Lab in the Humanities have created
Kits for Cultural History, physical kits with reconstructed components arranged in
wooden boxes, inspired by artists’ Fluxus kits (Fluxkits) of the mid twentieth
century [
Sayers 2015]. The kits depend on reverse engineering as one
phase in the ongoing process of dismantling and reconstructing historical
technologies and media in order to better understand their designs and cultural
meanings. For example, one kit allows the user to assemble a Victorian-era
skull-shaped electric-light stickpin, an early example of wearable technology. As
Sayers says, the kits “fabricate their own evidence off the page for assembly”
— the key phrase being “off the page”
[
Sayers 2015], that is, in the lab or workshop, but also in the conceptual space beyond any
available documentation. The kits “identify gaps in material culture and prototype the
absences for examination”
[
Sayers 2015]. You begin with already reverse-engineered parts and some limited forms of
documentation— designing, milling, printing, or otherwise fabricating the components
and putting together the kits in the first place, not just using them, is an
important phase in the process — then reconstruct the historical object, or, we
might more accurately say, construct models of the historical object. The kits
assume that historical knowledge is always provisional, part of an ongoing process
of analysis, disassembly, conjecture, and reassembly. The kits use digital as well
as physical components, including .OBJ and .STL files (shared via GitHub) that allow
for the 3D printing of tangible components. Investigators can 3D-print small
translucent skulls and wire them to batteries, for example, thereby raising
questions about Victorian power sources, fashion, and cultural attitudes.
Reverse engineering is similarly important in media archaeology, which grapples with
gaps, ruptures, and concealed, lost, or forgotten knowledge about media or
platforms. The concept appears explicitly in the work of Wolfgang Ernst to describe
a method of hands-on experimentation, as Jussi Parikka explains:
For Ernst media archaeology is not only a way of writing but
a method that has to do with reverse engineering. Hence his way of
approaching objects is not merely as a collector but as an amateur engineer
who opens, checks physically, tests, and experiments to learn how media
function. [In Ernst’s work] Foucault became employed as a technician, and
media archaeology incorporates DIY.
[Ernst 2013, 12–13]
Ernst believes that some media archaeologists have focused too literally on
the recovery of lost or forgotten technologies, based on a reductive interpretation
of Michel Foucault’s concept of archaeology. Rather than
techne,
Foucault emphasizes
episteme, the conditions that constrain knowledge
by determining what can be known [
Foucault 1969/2002]. For Ernst, it’s
important that media archaeology, as “both a method and an aesthetics of
practicing media criticism,” be recognized as “a kind of
epistemological reverse engineering”
[
Ernst 2013, 55] (my emphasis).
Media archaeology understood as an analysis of
epistemological configurations (both machinic and logic) does not simply
seek a redemption of forgotten or misread media of the past, nor is it
confined to a reconstruction of the crude beginnings and prehistories of
technical media. Rather than being a nostalgic collection of “dead media” of
the past, assembled in a curiosity cabinet, media archaeology is an
analytical tool, a method of analyzing and presenting aspects of media that
would otherwise escape the discourse of cultural history.
[Ernst 2013, 55]
The dual emphasis, on implicit epistemology and material particulars, allows
for the study of media in multiple dimensions. This takes into account larger
structures determining historical affordances and constraints, while, at the same
time, as Lori Emerson has put it, offering a check on our speculations through the
“sobering conceptual friction” produced by the method itself [
Emerson 2014, xii].
Geoffrey Rockwell and Stéfan Sinclair have called for a media-archaeology approach to
the study of Busa’s work, as part of “technology development around mainframe and personal
computer text analysis tools, that has largely been forgotten with the
advent of the web”
[
Rockwell and Sinclair 2014]. They argue this will help us to question narratives of inevitable progress
and to begin to “understand how differently data entry, output and interaction
were thought through” in the mainframe era. They have begun to experiment
with software emulations of Busa’s punched cards and their encoding systems,
extrapolating from these to speculate about the workflow into which the cards were
fitted. In fact, details of this most fundamental aspect of Busa’s method remain
obscure.
The point is to grapple with what we don’t know about Busa’s practice, including
roads he did not take, technologies from which he turned away but the existence of
which still sheds light on what he did. In addition to raising questions about
received narratives, media archaeology offers a way to study the component parts of
a technological system in analytical detail and as assembled wholes, to construct
arguments about the constraints and affordances that come with even apparently
insignificant component parts of the system. In the case of Busa’s work, these
include for example those iconic punched cards themselves, the key medium for data
input, output, and processing. But they also include the printing capabilities of
certain IBM machines, and the use of large-scale electronic calculating machines and
early computers, and the new medium of magnetic tape, for example, which made for
faster sequential processing of linguistic data at later stages, even when that data
had originally been punched onto cards. For Busa, the use of punched-card data
processing machines and room-sized calculators overlapped—as they did for many users
at mid century. Each system must be understood in relational terms, within an
environment combining multiple emergent with only partially displaced platforms.
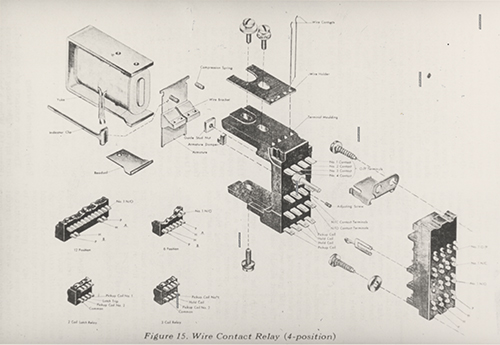
I’ve suggested elsewhere that a useful figure for what’s involved in reverse
engineering technological systems can be found in the
“exploded-view” diagrams used by engineers and patent
attorneys [
Jones 2016, 32–33]. These visualizations are metaphors
for the processes of disassembly/reassembly for which they also serve as practical
tools. They represent the component parts of a system, such as the IBM relay switch
illustrated in
Figure 2, as if they were blown apart, hanging
suspended in mid air, each part labeled and connected back to the ensemble of the
whole. This kind of 3D exploded-view diagram is often said to descend from the
famous notebooks of Leonardo [
Bogost 2012, 51]. We encounter
mundane versions today in instructions for assembling Ikea furniture or Lego kits,
as well as in schematics of scientific instruments and inventions, sometimes in the
form of 3D digital graphics programs. The exploded-view diagram is a visual
technique for representing technology, a technique that has itself become part of
the history of technology.
The Busa Archive contains almost one thousand high-quality photos, about eighty of
which specifically represent the center in Gallarate. As I mentioned above, the
building that housed CAAL’s main workspace was demolished by 2012, as Google Earth
and other sources confirm.
[3] The photographs in the Busa Archive, with a few limited
exceptions, show only the interior of that lost building, providing some evidence
for the layout, machinery, and equipment in Father Busa’s lab (as he often called
it). But we have to remember that those photos were commissioned and curated by Busa
himself. Each is like an idealized diagram of the center, including its layout and
workflow. When I visited the site in November 2017, a former punched-card operator
and supervisor, Livia Canestraro Tonelli, showed me her personal snapshot of the
lab’s interior, a much less formal view of the space than the commissioned photos
depict. I was struck by the image of two young women in the right foreground looking
straight at the camera, sitting side by side at the same IBM 024 Card Punch. In fact
there are three such pairs of operators in the photo. This differs in significant
ways from the look and feel of the Busa Archive photos, suggesting a more
collaborative working environment than those official images imply. Signora
Tonelli’s snapshot, shared with me half a century later on the site of the
demolished lab, vividly illustrates what we still don’t know about the actual
quotidian work of CAAL.
This is just one example of the need to take into account social arrangements and
human actors in their physical environments, as cultural archaeologists have always
done.
[4] Reverse engineering is effective as a method in so far as it
challenges assumptions, opens up alternative histories or counter histories, reveals
gaps in knowledge and experiments with filling them in, but with the seams showing,
like the polymer fills in 3D prints of reassembled broken pottery. The process is
iterative: any reverse-engineered model is designed to be questioned and perhaps
displaced by subsequent models. It’s the exploratory, heuristic process of modeling
that matters more than any given model, and the models are most useful at the limits
of knowledge, at the edge of productive ignorance.
[5]In those terms, what would it mean to reverse engineer the Center for Literary Data
Processing as a whole, as a technological system? To begin, we’d have to start with
the premise that technology extends beyond machinery to infrastructure and
institution, and even to the epistemological conditions, premises, and designs that
afford and constrain the system. The archival photographs, for example, show an
array of components, beyond machinery and punched cards, including chalk boards,
sorting tables, flowcharts and diagrams, floor plan, icons and decorative elements,
and human operators. Each component was part of the system but each implies its own
contexts, including the global institutional networks that were as important to the
center as the IBM machines. In the remaining space of this essay, I’ll use a few of
the photographs in the Busa Archive to sketch out some components of that implied
system, and suggest how a more thorough application of reverse engineering might
proceed.
I start with a personal snapshot, along with two of the archival photographs (a
larger selection is visible at
http://avc.web.usf.edu/images/RECAAL/): (1) my own snapshot of the
exterior of the remaining building at via Galileo Ferraris, 2, taken March 2015,
while it was undergoing renovation; (2) an image of IBM machinery’s being crated and
removed from the site in 1966 or 1967, as CAAL was closing at that location; and (3)
an image of the lab fully equipped and staffed with student operators in their white
coats, presumably taken in 1966 in the now-demolished building
Figure 1
Figure 3
Figure 4. So the sequence moves in reverse order, starting with the
remnant building in 2015, going back to the moment 48 years earlier when CAAL was
decommissioned, and then, perhaps only months before that, to a view of the full
configuration of the Literary Data Processing system as if in operation, as it had
been in that location for six years.
That last-named photograph of CAAL in operation (
Figure 4) can
itself be read as a system diagram. Indeed, the photo was professionally taken and
was likely staged by Father Busa as just such a diagrammatic tableau vivant. It was
taken near the very end of the center in that form, at that location. In the diagram
we see an array of components, from the peculiarities of the physical plant itself,
to the signs and symbols with which it as decorated, to the human operators or
“computers,” most of them young women, who performed the
processing, embodying what might once have been referred to as the “human
factor” of the data processing system.
The building at via G. Ferraris, no. 2 was once a textile factory, so it had a long
open-plan interior with a multiply peaked accordion-style roof with skylights to
optimize natural light down on the line. It was donated for Busa’s use (that is,
made available rent free) by a prominent local textile family with some additional
financing from another industrialist. Gallarate had been a center of the textile
industry for generations and Busa adopted the production-line layout for CAAL along
with the building, with grey-metal four-footed IBM punched-card machines instead of
looms and other textile processors. The scientific-industrial management model is
clear in the layout. Textiles gave way to texts, woven fibers were replaced by
skeins of words. It’s even possible that different kinds of punched cards were used
to program Jacquard-style looms there at one time (though I have no evidence of
this). The industrial plan shows in the details: the skylights, the power cables
dropped from the ceiling alongside columns, the rows of small heaters with chimney
pipes, even the open spaces around the edge of the room for worktables, where
textual piecework could be done “offline” (punched-card sorting
and concordance lemmatization), as well as the prominent station in a room to the
side of the main lab space with a desk for Father Busa—a kind of manager’s office.
That office also resembled a dais or altar. A number of photographs in the Busa
Archive commemorate a formal visit by Cardinal Colombo for the inaugural dedication
ceremony, and the back wall behind Father Busa’s desk eventually contained a large,
colorful stained glass window with electric backlighting depicting a modernist head
of Christ. That dominating icon is a reminder of the overarching importance of his
Jesuit order and the Catholic church when it came to the conception and mission of
CAAL. The decor of the lab reminds us of how industrial and religious cultures
combined to create the infrastructure of Busa’s project. In some photographs you can
see passages in Greek (one is Romans 11:36, for example) and Hebrew inscribed on the
wall on either side of the stained glass window. Perhaps none of this is surprising
in the lab of a researcher-priest. But the combination of cultural and industrial
influences is important. Those scriptural passages, for example, can be read as
religious alternatives to the inspirational workplace mottoes found all over IBM
headquarters, the best known of which was the THINK sign, which Busa would have seen
displayed everywhere while working in IBM in New York and Milan, including one
prominently hung over the desk of the founding CEO, Thomas J. Watson, Sr., when Busa
first met him in 1949 to propose the project and secure IBM’s support.
It’s difficult to disentangle the industrial culture of IBM at the historical moment
of its expansion into a global enterprise from the worldwide mission of the Jesuit
order, which included the tradition of founding schools, for example. The student
punched-card operators at CAAL were trained according to the IBM model, certainly,
but many of them came straight from the local Catholic school, and during their
two-year scholarships at CAAL they were required to take Theology and English
classes while receiving hands-on training in data processing. Siegfried Zielinski
has pointed out that the Renaissance Jesuit polymath, Athansius Kircher, S.J.
(1602-1680), exploited a “worldwide network of clients and patrons,” and
pursued his scholarship supported by the Jesuits’ “international network,” a “system of religious faith, knowledge, and politics,
combined with the development of advanced strategies for the mise-en-scène
of their messages, including the invention and construction of the requisite
devices and apparatus”
[
Zielinski 2008, 118]. The same description could be applied to Father Busa’s work three centuries
later.
Besides grants from local industrialists, CAAL received some small grants from the
Italian national government. But by far the chief financial support came from IBM.
This flowed from IBM’s newly founded World Trade Corporation but also through IBM
Italia in Milan, in whose borrowed offices Busa had originally started a precursor
to the center in 1954, while solidifying his agreement with IBM. For CAAL, IBM
provided free technical support, as well as the all-important endless supply of
paper punched cards (often called simply “IBM cards” at the time
in recognition of the company’s dominance of the worldwide market for them), and,
through a system of annual points, essentially gave Busa the use of data-processing
machines rent-free. It also made some additional financial contributions to keep the
center running [
Jones 2016, 113].
The photos in the Busa Archive sometimes reveal specific models of the machines, or
their nameplates suggest they were trucked in directly from IBM Italia in Milan.
Some show which source texts the operators used for input, and you can sometimes see
the patterns on punched cards as they were passing through the machines. These
machines were of course the key apparatus for the lab’s workflow. They were always
used in suites to process decks of cards in series: punching, copying, sorting,
printing, and collating. It’s of course impossible to tell from the photos every
combination of specific models used over the years—another example of the need for
conjecture and speculation. But they were mostly punched-card machines, starting
with the IBM model 024 and 026 Card Punch (the only difference being that the 026
had the capability to print onto the cards as well as punch holes in them), rather
than large stored-program computers, although some additional processing was done at
the company’s location in New York using the magnetic tape drive of the IBM 705 Data
Processing System, for example. In general, histories of computing have tended to
focus on well known large-scale machines that can be identified as ancestors of
later computers, ENIAC, UNIVAC, and so on. This has led to an underemphasis on
“normal” technological practice during the early years of
computing, such as the widespread use of technically out-of-date, lower-cost office
machinery, several generations of which remained in operation in commercial,
academic, and government settings for decades after the end of World War II. Indeed,
it was 1962 before IBM’s revenues from stored-program electronic computers overtook
its revenues from punched-card data processing systems [
Jones 2016, 117]. Busa’s humanistic project was one example of the kind of uses to
which punched-card machines continued to be put, well after the emergence of
electronic stored-program computing. In this context, out of both design and
necessity, the first humanities computing center could more properly be thought of
as a humanities
data processing center.
The Busa Archive contains a diagrammatic flowchart for “Mechanized Linguistic
Analysis,” as it’s labeled (see
http://avc.web.usf.edu/images/RECAAL/). It was produced at IBM in New
York in 1952, presumably for Father Busa’s first big demo in June of that year, nine
years before CAAL was established in Gallarate. Initials at the top
(“PT”) suggest that the diagram was drawn by IBM’s Paul
Tasman, Busa’s great collaborator for decades thereafter. The shapes of the boxes
drawn on the chart are conventional, representing different operations at various
stages in the process: documents (a rectangle with a wavy bottom edge), individual
punched cards, stacks of punched cards, machine operations, and so on. The chart
diagrams the process for creating the
Index Thomisticus
as it was first conceived, 1949-1952.
[6] While this may tell us something about the
later setup in Gallarate, the machinery and workflow were sure to have changed by
1961. Comparing the 1952 chart to similar flowcharts from later decades and using
Father Busa’s later accounts can help us to speculate about the setup at the center
in the 1960s, but only provisionally, as part of the ongoing process of historical
modeling. One thing evident in the 1952 flowchart is the human role, not just to
operate the machinery but at key stages to hand-sort the cards. One stage labeled in
the chart, set off by dotted lines, is “SCHOLAR WRITES ENTRY WORD LIST,” and in
fact the lemmatization of words in the
Index
Thomisticus, as well as a number of other sorting tasks, not to mention
simply carrying the cards from machine to machine between each stage, required human
effort. “Automation” at the time (as today) remained a
not-fully-realized ideal, a hybrid process involving the collaboration of human and
machine.
Despite the language on the flowchart, many of the human tasks at CAAL were
undertaken not by a “scholar” per se, but by the young student
apprentices who were also the machine operators. Most of them were young women. In
the photographs we can see them in white lab coats at the keypunches, but also
facing one another at tables off to the side, apparently sorting cards by hand. In
1961, the operators worked in two four-hour shifts per day, punching and verifying
the cards. The system was hierarchical and gendered, in line with the gendering of
all data processing at the time. Three special operators were selected from among
the ranks as supervisors [
de Tollenaere 1963]
[
Jones 2016, 124]. Chief among these was Livia Canestraro, who
had been one of the earliest students in the training school, from before it was
established at the via Ferraris site. In a recent interview conducted by Julianne
Nyhan and Melissa Terras, she tells an interesting story of Father Busa’s attempting
sometime in the 1960s to replace her with a young man, an attempt stopped by a
rebellion among the students, including, she says, some of the minority who were
men. She notes that she’s grateful for the opportunities she had, rare at the time
for a young woman, but she still regrets the lack of a “real
diploma” from the Center, despite all her training and practical
expertise; in the end, she says, she “was interested in women’s ... being able to
do the same tasks as men” — implying that the culture and workflow of CAAL
did not support this ideal [
Nyhan and Terras forthcoming]
[
Jones 2016, 124]. After leaving the center she went on to work
as an editor.
Canestraro was the exception. There’s no evidence that any other women at CAAL held
more senior roles, let alone crossed over to the scholarly side of the center’s
organizational structure, which was located up the road at Father Busa’s Aloisianum
college (named for Saint Aloysius Gonzaga). So there was a two-tiered structure:
technical workers down at the factory, and scholarly or intellectual supervisors up
at the college. Women were the usually invisible or anonymous laborers of all early
computing, and many of the official archival photos are telling in this regard. The
operators sit at the machines with their hands on the keyboards and their heads
down, while suited male conferees or visitors stand around watching the
demonstrations. Along with these photos, the transcripts of Terras's and Nyhan’s
interviews with some of these women give us a more detailed, alternative story to
complicate the received founding narrative [
Nyhan and Terras forthcoming].
The photos in the Busa Archive reveal CAAL’s odd mid-century aesthetic, a combination
of the industrial and the homemade. Card-file cabinet doors along the side of the
room appear to have been exuberantly hand painted. Abstract shapes drawn high up on
the surrounding walls resemble puzzle pieces whose outlines contain characters from
various languages, some recognizably Hebrew, Roman, or Greek. These may have been
meant to invoke linguistics in general, or the idea of textual fragments, the
partial and incomplete state in which all texts descend to us through history. They
may also represent texts as deliberately “blown to bits” —
exploded into their constituent signs, precisely the kind of atomization that was
part of the automation of linguistic processing, the concordance- and
abstract-making of the center. In this sense, the icons may represent language as
bits of data to be processed.
More immediately, I suspect they were meant to invoke the recently unearthed Dead Sea
Scrolls, fragments of which CAAL had started working with at the time (There are
photos in the Busa Archive showing arrays of some of those fragments that look very
much like the drawings). That Dead Sea Scrolls work never resulted in a published
index, due to personal problems on Busa’s part and the various competing interests
in which the primary materials were entangled [
Jones 2016, 163–65]. But the project offered Busa a new perspective on data processing and a new set
of philological questions. It required transcripts—themselves not easy to come by at
the time—to be marked up and customized punched cards for Hebrew and Aramaic texts,
as well as the customization of machines so that the Hebrew-punched cards could be
read right to left. The Dead Sea Scrolls work was a significant if relatively small
project for IBM, too. The company capitalized on its sponsorship in the 1960s, as
seen in one print ad touting the work under the headline of solving “literary
puzzles”
[
Jones 2016, 139–40].
Father Busa saw the work of CAAL as aspiring to a new kind of computerized philology.
Philology is a term that carries a good deal of historical baggage [
Jones 2016, 154–56]. For Father Busa it seems to have meant
simply the study of natural language in its minute particulars and cultural
contexts, and he believed that, through quantification, computing had opened up a
“new dimension” that made a qualitative difference [
Busa 1990]. The philological remit of CAAL led to some work in machine
translation, which was tied to the rise of Natural Language Processing.
Experimentation in this area was widespread until the Automatic Language Processing
Advisory Committee (ALPAC) report of 1966 determined that its funding should be
curtailed. In 1954, at the moment Busa was first working to establish CAAL, IBM held
a widely publicized demonstration of machine translation featuring a team of
researchers from Georgetown University’s Linguistics group. An IBM 701 Defense
Calculator was used to translate into English a group of Russian sentences, based on
a limited set of syntax rules. As the press release put it, a
“girl” who didn’t understand Russian was deliberately chosen,
so that she could mechanically punch the Russian sentences onto cards. The
“electronic ‘brain’” then “dashed off its English
translations on an automatic printer at the breakneck speed of two and a half
lines per second.” The press release also pointed out that the machine had
interrupted its schedule of calculating rocket trajectories in order to address this
“new and strange realm,” as it called it, “the human use of words”
[
Jones 2016, 110].
In the Cold War era, even humanistic research of this kind was likely to be defense
work. At the beginning of the new decade Father Busa personally brokered an
arrangement between the IBM-Georgetown group and both the U.S. Atomic Energy
Commission and Euratom (European Atomic Energy Community, founded by treaty of
1957), located in Ispra, about 30 kilometers northwest of Gallarate. Busa later
recalled that he made the connection, as he said, “on an exchange
basis,” serving as liaison and facilitator of the arrangement [
Jones 2016, 111–12]. He drew up on paper a formal agreement among
the parties, with CAAL as a central node in the network thereby established. The
student operators at Gallarate punched onto cards about a million words of
Russian-language texts. The cards were then processed by the Georgetown-IBM system
at Ispra. In return, CAAL appears to have received some funding from Euratom, and
some of the punched-card operators were later hired at Euratom when they left CAAL
[
Jones 2016, 111–12].
What Father Busa called the “exchange basis” through which he made
this series of connections can be understood as a kind of educational or diplomatic
exchange, in which CAAL’s students and its operating budget benefitted as a result
of providing certain services. Indeed “exchange” also suggests
the resources and currencies involved. But metaphorically, we might also say that
Father Busa served as an “exchange” in the technological sense, a
kind of switch or relay for traffic, as in a railroad or telephone exchange. Or the
plugboard system of a data-processing machine, examples of which can be seen in the
Busa Archive photographs. At mid century, manual matrix exchanges were still in
widespread use, by which human operators could make complex series of connections on
large plugboards by changing the configuration of wired plugs, a kind of hardwired
programming. Some models allowed for the boards to be lifted out by a handle and
carried by operators and installed in a new machine, so that a given configuration
could be transferred. The first humanities computing center, CAAL, only existed at
the site on the via Ferraris for about six years. In the 1960s, however, it served
as a router for many such exchanges.
I’m now collaborating with a team of researchers from four countries with the support
of an NEH Level II Digital Humanities Advancement Grant (2017-2019), working with
the University of South Florida’s Advanced Visualization Center to create immersive
3D models of the site of Busa’s center and its machinery. These models will be
integrated with a range of other materials: Geoffrey Rockwell and Stéfan Sinclair
are experimenting with emulations of Busa’s process and workflow, as I’ve said, and
Melissa Terras and Julianne Nyhan have already been reconstructing the history of
Busa’s female punched-card operators, including conducting interviews with some of
them. At the Università Cattolica del Sacro Cuore in Milan, Marco Passarotti and
Paolo Senna are working to digitize primary materials in the Busa Archive. The
result of this collaboration will be a kind of virtual lab within which to
experiment with reverse engineering the technologies and institutions that made up
Busa’s famous (but only dimly understood) center and its work.
Already a more nuanced and detailed understanding of CAAL has begun to emerge,
challenging the simple founding narrative of humanities computing and shedding new
light on today’s digital humanities and on issues of institutionalization, funding,
and labor. Our modeling starts with the minute particulars of material technologies
and extends to wider social and historical contexts. The first Center for Literary
Data Processing was the product of strategic alliances, pragmatic arrangements, and
social connections, as well as available machinery and material infrastructure, all
framed by Father Busa’s Jesuit mission, academic notions of the humanities, and
models of industrial productivity. Evidence of these system components can be found
in the images and other documentation, from the floor plan of the now-demolished
former factory, to the arrangement of machines on the floor, to the decks of punched
cards flowing through it all by way of combined machine and human agency—including,
centrally, but never exclusively and never in isolation, the agency of Father Busa
himself. The via G. Ferraris, 2 remains an important site in the history of
technology and the humanities, and it’s a site we’ve only just begun to
understand.
Works Cited
Bogost 2012 Bogost, Ian. 2012. Alien Phenomenology: Or What It’s Like to Be a Thing.
Minneapolis and London: University of Minnesota Press.
Busa 1951 Busa, Roberto, S.J. 1951. Sancti Thomae Aquinatis Hymnorum Ritualium Varia Specimina
Concordantiarum: A First Example of Word Index Automatically Compiled and
Printed by IBM Punched Card Machines. Archivum Philosophicum
Aloisianum. A cure della Facultaà di Filosofia dell’Instituto Aloisianum S.J.
Serie II, N.7 Fratelli Bocca: Milan.
Busa 1990 Busa, Roberto, S.J. 1990. “Informatics and New Philology.”
Computers and the Humanities 24,5-6 (December
1990), 339-43.
Emerson 2014 Emerson, Lori. 2014. Reading Writing Interfaces: From the Digital to the
Bookbound. Minneapolis and London: University of Minnesota
Press.
Ernst 2013 Ernst, Wolfgang. 2013. “Media Archaeography: Method and Machine versus the History and
Narrative of Media.” In Digital Memory and the
Archive, 55-73. Ed. Jussi Parikka. Electronic
Mediations, Vol. 39. Minneapolis and London: University of Minnesota
Press.
Foucault 1969/2002 Foucault, Michel. 1969; 2002.
Archaeology of Knowledge. Trans. A.M. Sheridan
Smith. Routledge Classics. London and New York, Routledge.
Jones 2016 Jones, Steven E. 2016. Roberto Busa, S.J., and the Emergence of Humanities Computing:
The Priest and the Punched Cards. New York: Routledge.
Mattern 2017 Mattern, Shannon. 2017. Code and Clay, Data and Dirt: Five Thousand Years of Urban
Media. Minneapolis and London: University of Minnesota Press.
McCarty 2004 McCarty, Willard. 2004. “Modeling: A Study in Words and Meanings.” In
A Companion to Digital Humanities. Eds. Susan
Schreibman, Ray Siemens, John Unsworth. Oxford: Blackwell,
http//digitalhumanities.org/companion.
Nyhan and Terras forthcoming Nyhan, Julianne
and Melissa Terras. Forthcoming. Uncovering Hidden
Histories of the Index Thomisticus: Busa’s Female Punched Card
Operators.
Terras and Nyhan 2016 Terras, Melissa and Julianne
Nyhan. 2016. “Father Busa’s Female Punched-Card
Operators.” In
Debates in Digital Humanities
2016. Eds. Matthew K. Gold and Lauren Klein. Minneapolis and London:
University of Minnesota Press,
http://dhdebates.gc.cuny.edu/debates/text/57.
Winter 1999 Winter, Thomas Nelson. 1999. “Roberto Busa, S.J., and the Invention of the Machine-Generated
Concordance.”
The Classical Bulletin 75,1 (1999), 3–20.
Zielinski 2008 Zielinski, Siegfried. 2008.
Deep Time of the Media: Toward and Archaeology of
Hearing and Seeing by Technical Means. Cambridge, MA: MIT
Press.
de Tollenaere 1963 de Tollenaere, Félicien.
1963. English typescript draft for Nieuwe wegen in de
lexicologie. Amsterdam. Busa Archive.